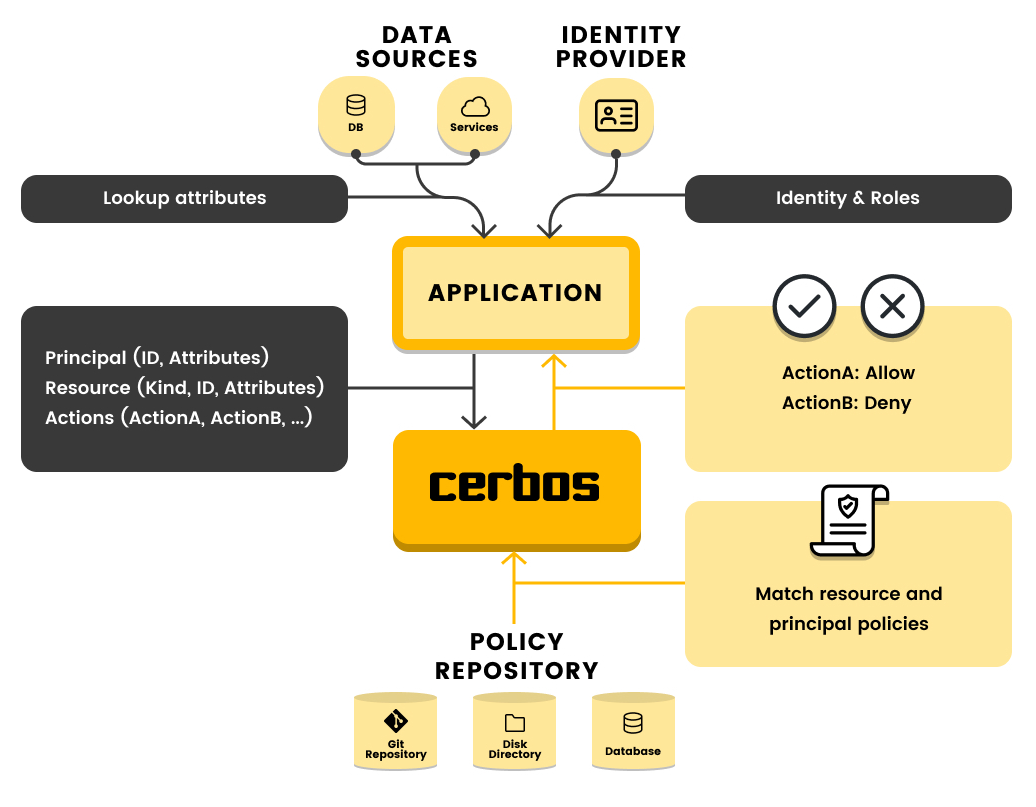
This Golang Opensource Project helps you to
Super-charge your authorization implementation
by writing context-aware access control policies for your application resources. Author access rules using an intuitive YAML configuration language, use your Git-ops infrastructure to test and deploy them and, make simple API requests to the Cerbos PDP to evaluate the policies and make dynamic access decisions.
- Try online with the Cerbos playground
- Explore demo repositories
- Read the documentation
- Subscribe to the newsletter
- Join the community on Slack
- Install Cerbos
- Container
- Binary/OS packages
- Helm Chart
- Get the client SDKs
- Contribute
Example Configuration
Derived roles: Dynamically assign new roles to users based on contextual data.
---
apiVersion: "api.cerbos.dev/v1"
derivedRoles:
name: common_roles
definitions:
- name: owner
parentRoles: ["user"]
condition:
match:
expr: request.resource.attr.owner == request.principal.id
- name: abuse_moderator
parentRoles: ["moderator"]
condition:
match:
expr: request.resource.attr.flagged == trueResource policy: Write access rules for a resource.
---
apiVersion: api.cerbos.dev/v1
resourcePolicy:
importDerivedRoles:
- common_roles
resource: "album:object"
version: "default"
rules:
- actions: ['*']
effect: EFFECT_ALLOW
derivedRoles:
- owner
- actions: ['view', 'flag']
effect: EFFECT_ALLOW
roles:
- user
condition:
match:
expr: request.resource.attr.public == true
- actions: ['view', 'delete']
effect: EFFECT_ALLOW
derivedRoles:
- abuse_moderatorAPI request
cat <<EOF | curl --silent "http://localhost:3592/api/check/resources?pretty" -d @-
{
"requestId": "test01",
"includeMeta": true,
"principal": {
"id": "alicia",
"roles": [
"user"
]
},
"resources": [
{
"actions": [
"view"
],
"resource": {
"id": "XX125",
"kind": "album:object",
"attr": {
"owner": "alicia",
"public": false,
"flagged": false
}
}
}
]
}
EOFAPI response
{
"requestId": "test01",
"results": [
{
"resource": {
"id": "XX125",
"kind": "album:object",
"policyVersion": "default"
},
"actions": {
"view": "EFFECT_ALLOW"
},
"meta": {
"actions": {
"view": {
"matchedPolicy": "resource.album_object.vdefault"
}
},
"effectiveDerivedRoles": [
"owner"
]
}
}
]
}Telemetry Settings
We collect anonymous usage data to help us improve the product. You can opt out by setting the CERBOS_NO_TELEMETRY=1 environment variable. For more information about what data we collect and other ways to opt out, see the telemetry documentation.

